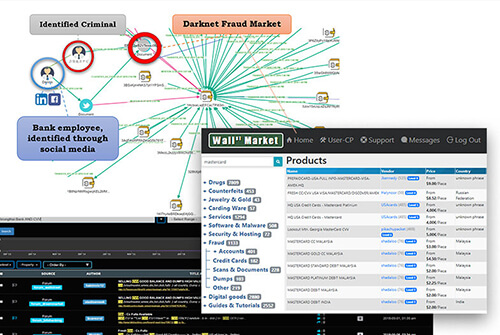
A research conducted by S2T Analytics found that several prominent Banks in Singapore have been targeted by the notorious malware, known for stealing banking credentials. The malware uses dark net domains in order to keep its C&C servers anonymous.
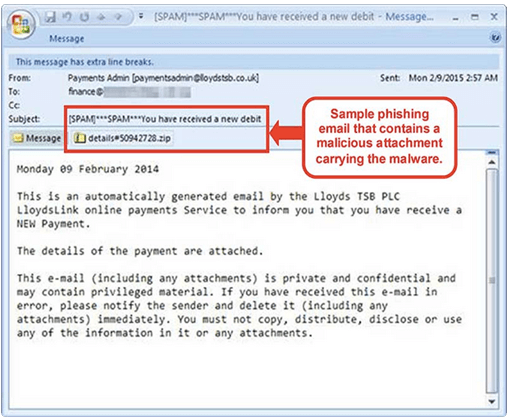
On February 12 2015, DBS bank released an announcement, stating: “We have discovered a variant of Dyre malware that may affect the legitimacy of the DBS IDEAL website. This malware is spread through phishing emails with malicious attachment. A sample of the phishing email is shown below. When the said malicious attachment is opened, the malware infects the customers’ computers or devices.” The company’s announcement also went on to explain the attack vector used for stealing the clients’ credentials: “Once customers’ computers or devices are infected, the malware will attempt to steal the customers’ login and authorisation credentials (such as Organisation ID, User ID, PIN, Security Access Code, SMS OTP and Challenge/Response) by altering the flow of logging on to the DBS IDEAL website. After the first login page, it will show a different “Security Access Code” page followed by a message that says “We are currently processing your information, please wait....” which does not exist in the legitimate DBS IDEAL website.”
Dyre, also known as Dyreza, is a banking Trojan that was first seen around June 2014. With the combination of its ability to steal login credentials by browser hooking and bypassing SSL, its man-in-the-middle (MITM) proxy server, and its Remote Access Trojan (RAT) capabilities, Dyre has become one of the most dangerous banking Trojans.
The Dyre Trojan is designed to steal login credentials by grabbing the whole HTTPS POST packet, which contains the login credentials sent to a server during the authentication process, and forwarding it to its own server.
The malware downloads a configuration file containing a list of targeted bank URLs. Each URL is configured to be redirected to Dyre’s MITM proxy server, on a different port for each bank. This allows the attacker to make a MITM attack by forwarding any user request to the bank and returning bogus data, including fake login pages, popup windows, and JavaScript/HTML injections. After all the information has been acquired by the attacker, he can remotely access the victim’s computer using a built-in VNC (Virtual Network Computing) module and perform transactions, data exfiltration, and more.
In early June 2014, researchers discovered that Dyre was being distributed by Cutwail botnet spam emails that included links to either Dropbox or Cubby file storage services. The threat actors later shifted to distribution via the Upatre downloader trojan. Recent, more developed versions of Dyre use SSL to encrypt all C2 communications, as well as a custom encryption algorithm.
Moreover, a recent version of the Dyre banking Trojan, delivered via phishing, has been seen to integrate communication through the I2P anonymization network. I2P is an overlay network similar to Tor that offers anonymity. It provides anonymous hosting known as eepSites, which are similar to Tor's hidden services. eepSites allow users to access websites in a way that masks the true location of the server, so that it cannot be easily identified and taken down.
Samples of the malware collected in the past two weeks, have shown that several prominent Singaporean banks in addition to DBS, were found among those targeted by the threat actors. Such campaigns also involved the implementation of i2p C&C servers.
Several Singapore banks in addition to DBS were targeted by Dyre according to the information collected by S2T Analytics from Internet sources and closed forums.
Though Dyre’s stealthy architecture makes it hard to discover possible infection, there are several recommended measures for mitigating this threat:
- Increase clients’ awareness for phishing methods, since the malware is often downloaded as an email attachment, in addition to implementing the use of fake websites which resemble the bank’s
- Monitoring potential signs of infection, such as connection to a compromised IP address or domain. (see attached list below)
- S2T offers its expertise and experience in data harvesting from the deep and dark web for monitoring developments and trends concerning financial cyber-threats. Such monitoring may help substantially in better preparing for potential attacks.